What Is OAuth (Open Authorization) and Why Is It Important?
Data breaches are one of the biggest threats in a fast-rising and technologically advancing generation. A data breach can devastate businesses, reputations, and even governments. Moreover, it takes a single vulnerable, privileged account to be compromised by unauthorized entities for critical data to be “stolen.” The digitized world generates, shares, stores more data, and digital accounts are common.
Many services on the internet are integrated and designed to interact with one another. However, using service accounts to access applications and websites involves the unsafe practice of storing privileged credentials, primarily without multi-factor authentication (MFA), and exposes private information to compromise.
The importance of privacy and data security is incredible. Consequently, open security standards like OAuth secure personal and private information during data transfer between third parties. The OAuth standard compiled by the Internet Engineering Task Force (IETF) protects resource owners on the web while using third-party services. Keep reading to find out more about OAuth.
What Is OAuth?
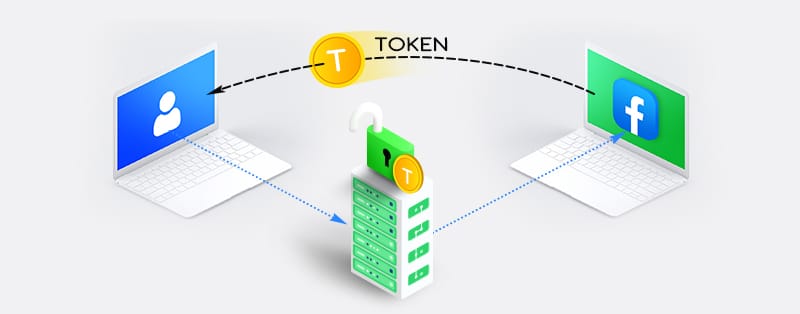
OAuth (Open Authorization) is an open standard framework that allows third-party access to authenticated user-related information or assets on servers and services (like websites and applications) without sharing their login credentials. It provides secure delegated access to server resources on behalf of a resource owner using token-based authentication. However, authentication protocol verifies user identity using passwords, phone, or biometric identity and should not be mistaken for Open Authorization protocol.
As opposed to authentication protocols like OpenID, OAuth authorizes limited access to resources after successful authentication. Companies like Facebook, Google, Amazon, Twitter, Paypal, Netflix, and Microsoft permit their users to share account information with third-party websites and applications through OAuth.
OAuth’s decoupled authentication and authorization standard protect user information by granting access to resources without revealing the user’s identity or credentials. Hence, third-party services can request a user’s behalf without accessing passwords and other sensitive information.
The OAuth mechanism follows an authorization flow with three key components: the provider, owner/user, and client/consumer. The OAuth provider is the authorization server and main engine of OAuth. Resource servers (APIs like Facebook or Google) use OAuth to connect to a third-party website or application on a user’s behalf and approval. The provider gives the client service an access authentication token for authorization to information hosted by the resource server. The User owns the data/information in a resource server. The user’s login confirms sharing of information. The Client is the website or application that requires access to the user’s information or resources.
It gains access to the resource server with an access token. Finally, the client program requires registration with OAuth for the authorization to proceed. The complete OAuth process requires multiple approvals and all three components for authorized transaction/access.
OAuth 1.0
The security of user information is essential with the increase in data sharing, storage, and utilization. As a result, it is important to integrate secure authorization standards into applications and website services to prevent data breaches. OAuth is recognized as the most secure information-sharing standard for websites and APIs. The OAuth standard supports multiple flows to address varying client app authorization scenarios and different device capabilities. It supports server-to-server apps, web apps, mobile apps, websites, consoles, or TVs.
OAuth 1.0 protocol was published in 2010 to topple the absence of open standards for API access delegation. However, it was first released in 2007 as an authorization method for the Twitter application interface. The IETF released OAuth 2.0 two years later as an improved and completely new authorization protocol. It differs from the first version with increased OAuth flows, short-lived tokens, and backward incompatibility with OAuth 1.0.
OAuth 1.0 handled delegation with a framework based on digital signatures. It was strong and secure that major players such as Google and Twitter supported and adopted it. It required crypto-implementation and crypto-interoperability, which made it very secure. However, it is challenging for developers to implement without adequate experience in cryptography and key management capabilities.
OAuth is generally a delegation protocol that provides permission and not an authentication protocol like OpenID– an identity layer built on top of the OAuth 2.0 protocol. Although many applications use OAuth 2.0 for authentication and authorization, it is only specialized for delegated authorization.
The OAuth 2.0 Framework
The OAuth 2.0 framework is the industry-standard protocol for authorization. A rewrite of the original Open Authorization protocol provides a more comprehensive solution for modern web and non-web clients. The framework contains specifications that further secure user data. These include:
Token Expiration
OAuth tokens are generally irrevocable, and in 1.0, they do not expire. As a result, the tokens are not totally secure and are prone to threats. With access to a token or verification secret, an unauthorized client/user, such as hackers and malicious sites, can make unauthorized requests and gain access to users’ credentials and personal information. OAuth 2.0 framework overcomes this weakness with expirable tokens. Once the access token expires, so does access to the application unless another access token is generated via the refresh cycle. OAuth 2.0 generates “short-lived” access tokens. They last between the duration of a session to a couple of weeks but utilize refresh tokens to acquire a new access token rather than have the user repeat the entire process to reauthorize the application.
Client-Side Development
OAuth 2.0 considers non-web clients as well as web workflows. OAuth 2.0 offers specific authorization flows for web applications, desktop applications, mobile phones, TVs/consoles, and non-browser-based applications such as API-based services. It is also much easier to implement, work with and provide strong authentication.
Separation of Duties
OAuth 2.0 separates the duties of resource delivery and handling user authorization. Physically separate servers, or even different domain names, can handle both roles. So, each part of the system scales independently. Hence, the authorization server requires the client ID and secret, but the API server will only accept access tokens. Consequently, the database evades data sharing with the API servers. These make the new standard more applicable for large enterprises. This is because it enables these systems to happen independently, by different teams, and on different timelines.
Bearer Tokens and Eliminated Cryptographic Requirements
OAuth creates a balance between easy use of APIs and good security practices. The use of bearer token simplifies the implementation of OAuth by eliminating the complexity of cryptographic signatures in OAuth 1.0 standards. OAuth 2.0 requires only the token itself in the request.
Two-Factor Authentication
OAuth used the less secure single-factor authentication method for the disclosure of accounts. The single-factor authentication could be compromised easily since hackers only need to obtain one piece of information to gain access. OAuth 2.0, however, requires more levels of authentication to give access to a user. It uses tokenization and a two-factor nature to secure user accounts.
Why Is OAuth Important?
Sophisticated web applications, mobile apps, and unique business models have emerged. The evolution of use-cases into new scenarios renders traditional authorization cogs inadequate. Many of these scenarios require a server or client to communicate(tap into) with multiple servers to execute a request or action. The need to provide new solutions for sharing data and federating identity among multiple trusted parties is, as a result, intensified. OAuth is a powerful security framework that strives to solve the challenges associated with authorization. Hence, it is important to integrate OAuth into applications and websites. Here is why:
It secures server information even while sharing
The OAuth protocol depends on SSL (Secure Sockets Layer) to ensure data between the web server and browser stay private. As a matter of fact, it is an important piece of any organization’s website authentication because it protects users’ credentials.
Tokenization permits only limited access to user data
Sensitive information such as credit card information and medical records are each assigned token IDs and stored remotely. Merchants receive the tokens, not the actual data. Hence, the information shared remains private. Third parties who do not have access to their medical records, passwords, or credit card number yet, can verify the token for transactions.
OAuth allows the use of single sign-on (SSO)
SSO ensures easy access, controls risks, and gives users control over their data. It enhances users’ morale and productivity by enabling access to multiple applications with only one set of login credentials. It consolidates user credentials and streamlines the login process for users. This eliminates the hassle of managing numerous passwords or repeating the same information while using online services.
It puts the users in control of what third-party services can do to their resources
Traditional processes require sharing credentials with third-party websites to share information. However, OAuth restricts third parties and prevents them from performing certain nefarious actions such as changing user settings or changing user credentials, and blocking user access to the account.
Conclusion
OAuth (Open Authorization) protects user information from data breaches as much as possible. The first protocol for OAuth 1.0 was rewritten into OAuth 2.0. The cybersecurity industry adopts OAuth 2.0 widely as the most secure option for authorization. Although there is no foolproof authorization system, OAuth is one of the best. Sites such as Facebook, Twitter, LinkedIn, Google, Amazon, Instagram, and GitHub use OAuth as their primary technology for authentication and authorization.